
The “Buttplug hacker” reveals how and why he did it
There’s lots of talk these days about cyber-security and the apparent ease with which computer hackers can slide malware and viruses through the myriad of network-connected devices that most of us have. When you consider that pretty much everything now comes with network capability – and we mean everything – it was only a matter of time before some clever clogs was able to crack the code and hack your buttplug. That clever clogs is smea.
For a little bit of background to this one, we’ve got to take you to DEF CON 2019. Held at Las Vegas’s Paris Hotel & Casino, DEF CON is the big conference for hackers everywhere. One of the hottest tickets at this year’s event was a presentation by a hacker named smea.
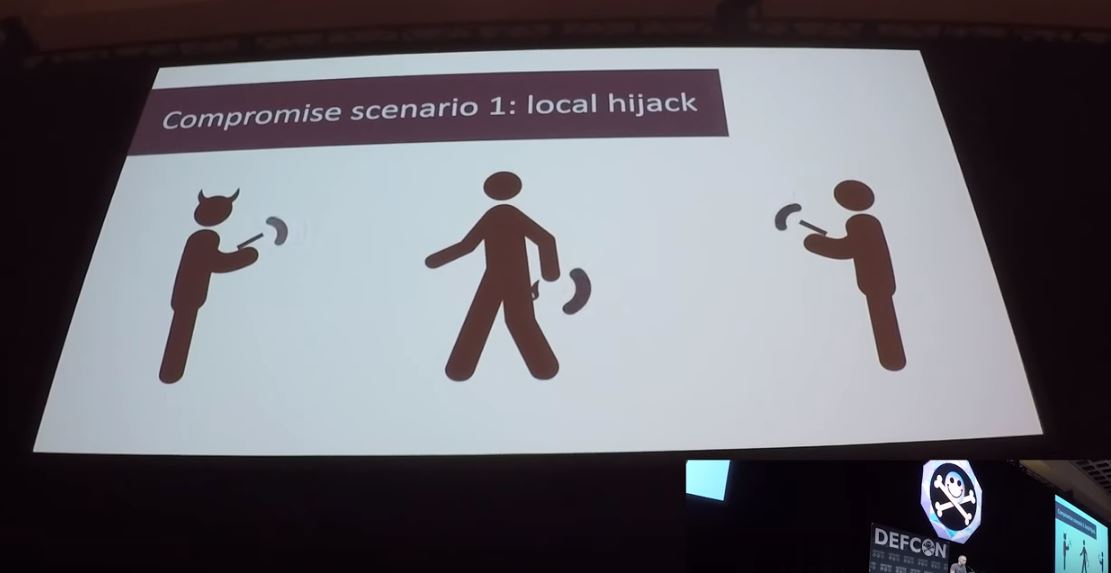
Credit: smea
Smea, previously known for his work as a security-oriented hacker on Nintendo consoles like the Wii U and 3DS, spoke about the security threat smart sex-toys may present. You know, what if hackers can access your network through security flaws in buttplugs, in turn, allowing them to spread all sorts of chaos.
He came up with the idea after realising many smart devices have weaknesses in their dongle.
“The idea was that…there’s nothing preventing you from uploading your own code to the dongle. From there, you can actually compromise the dongle back over Bluetooth using an actual vulnerability that’s found in the implementation of the Bluetooth low energy protocol (BLE) by Nordic Semiconductor — the manufacturer of the actual chip that’s used by both the dongle and the sex toy. So that’s an actual real vulnerability that could potentially affect other devices.”
While we’re not exactly sure if any of the following is even remotely possible, it’s about time we hit the panic stations on this kind of stuff. If hackers can access your buttplug, we’re going to ASSume there’s nothing stopping them from installing software that connects to your phone and records you every time you jam that little bugger right up your cloaca.

Credit: smea
From there, an upload to the world’s kinkiest websites – and your Facebook profile – is only a few steps away. Now, again, we want to reiterate that might be entirely false. Of course, the flipside of ‘might’ is that it might also be entirely true.
If you wanna know just how much smea can do through your buttplug, check this out:
“What I was doing in the demo is downloading an .exe file from the internet, and I just ran it because there’s no sandbox involved. I can just do that without actually having to exploit Windows or anything. From there, yes, I can actually compromise other applications on the device, do actual ransomware, encrypt all the files and stuff like that. It basically allows you to access every file on the system.”
So, what does this mean for you guys? According to smea, there’s a slight chance safety features in sex toys could be switched off – and if you’ve seen the new Chucky movie, you know how that ends.
“One of the things I brought up during the conference was that gaining access to the sex toy might allow you to bypass some safety features and that could cause physical harm, assuming those safety features were implemented in software. I don’t think that’s really necessarily possible with these [buttplugs], but you have other devices that have motors that are meant to rotate parts of the toy and stuff like that. If those have safety features implemented in software that could be a real problem.”
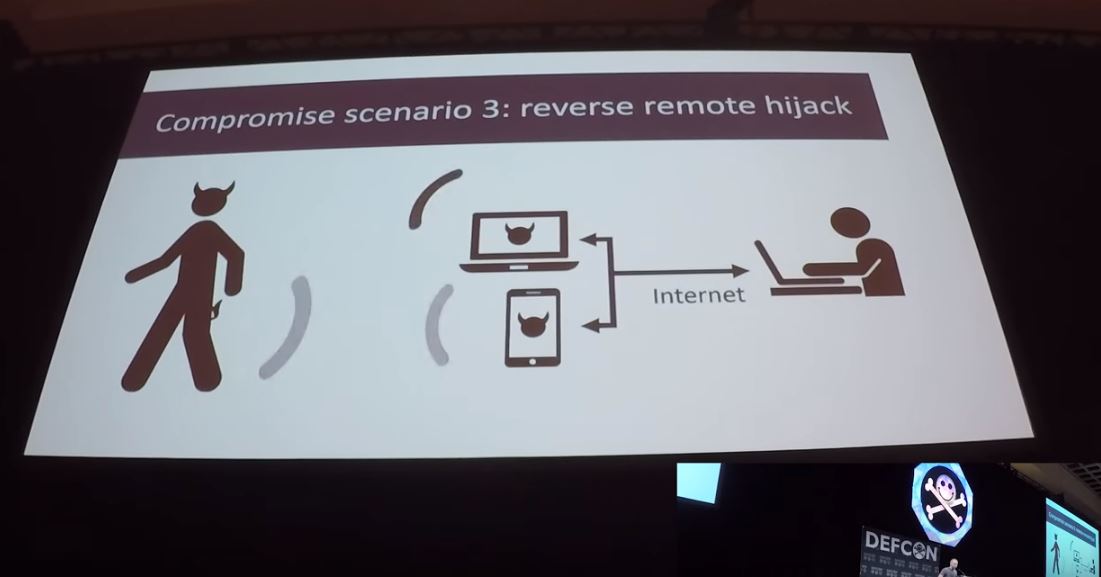
Credit: smea
Final thought: It seems that there’s a risk in everything these days, and that’s something we as consumers need to get used to. Is someone going to turn your king dong into an automatic weapon? Probably not. Could they access your other files? Maybe. We guess if you just keep it turned off when you’re not using it, you’re probably gonna be fine.
Just in case you missed it, here’s one of Ozzy’s latest commentary videos…Ozzy Man Reviews: Live TV Fails
Video Link: Cameron Saman
H/T: GIZMODO.












